I’ll be writing a daily summary post for the next few days. They may not be as long, but will try to give you my perspective on the events at RSA.
Table of Contents
The Vibe
It isn’t everyday you can go to a movie theater and attend a security conference, but at BSidesSF that is the case.
This year I made a commitment to attend some talks, because we can always learn something new, and even attend a technical workshop. It did help that I knew the workshop presenter, thanks to Pacific Hacker meetups.
Not only that, but where else can you have a geeky conversation about theater technology but with a bunch of security nerds! I love that. We debated between IMAX Laser in SF and 70MM IMAX in the East Bay. This is a common conundrum I run into where there a (Only in IMAX move I want to see). I love this community!
The vibe was really positive overall. People are really happy to come out. Lots of old faces and some faces I haven’t seen in awhile. Way more villages than ever before which is amazing! Lots of first timers as well.
📢Interested in Sponsoring? Email [email protected] We have 2 slots available this week.
Volunteering At BSidesSF
This is the first year in many that I am not volunteering at BSidesSF (need to manage my energy levels).
I actually fell into volunteering accidentally when one day at the end of the con one of the organizer, Liza, pulled me and asked if I can help them in a pinch. Some volunteers had not showed up (happens every year) and they were understaffed. As one who has a hard time saying no and a love for helping people, I of course said yes. Ever since then I volunteered my time at BSidesSF thereafter.

Liza Roberts, long time staff at BSidesSF and BSidesLV
I missed her last year and thought she moved on from BSides, so I was ecstatic to see her this year. I regard her as one of those good humans in infosec.
Thank you Liza and the entire BSidesSF Staff for all you do!
Select Talks
It would be hard to summarize the entire event, especially so early, so here is an attempt to give you some insight into some talks I had the opportunity of attending.
Talk: Insecurity Protocols - An Overview of Modern Authentication
So if it wasn’t clear, yes all the talks are held IN the movie theaters. As I’m writing this I am in the Dolby Cinema theater attending “Insecurity Protocols: An Overview of Modern Authentication”. Identity and Access Management (IAM) is a long time favorite of mine, so it seemed like a good place to commiserate in the vulnerabilities we see everyday. Although technically, it’s usually more of a misconfiguration issue than inherent “vulnerabilities”.
This was a speedy talk that went through all the authentication protocols and provided an overview of each and vulnerabilities and exploits in the past with each one.
A view of the talk from the Dolby Cinema theater
Quick Takeaways
Implicit Flow is dead
Beware of OAuth in SPA’s (Single Page Apps)
Just because there’s an RFC for something doesn’t mean you should do it! 😅
Did you know you can do a SAML assertion in OAuth??
Use of ID Token outside of OpenID Connect is common
OpenID Connect + JWT - ruh roh
F*&CK SAML (Author’s words, not mine!)
“Signature is inside the signed object, which does not make sense”
Namespaces and Canonicalization is complicated
Unsigned responses are totally valid!
SAML is riddled with auth bypasses (see list in the video)
FIDO2 - Best example of “modern authentication”
Passkeys
“A product manager took a bong hit and said
What if we could take FIDO credentials and put them in software?““Security keys make bad passkeys”
Passkey interoperability is still not fully there yet
TPM
TPMs are incredibly complex
Hardware attestation is common
Workshop: Kubernetes Security
I had the opportunity to attend the Kubernetes Workshop by Lenin Alevski. Two hours is not enough for such a deep workshop, but don’t fret. If you missed it, the entire lab is available on Github!!
Again I was in awe of seeing a terminal screen on a giant movie screen. Although some may thing that’s too big 😅
Talk: Temporary Access To The Cloud
The Chime security team has created their own temporary access manager to resources similar to Segment and Discord’s that hinges on Okta’s access. The presenter talks about the why and the process and presents a demo of the application as well.
I have personally tackled this problem time and again and it’s a constant pain point for security teams worldwide, so I was very curious on this talk.
Takeaways
64% of breaches are from insider access (not malicious)
Heavily influenced by Segment’s Access Services
Should be doing more cross-company collaborations
Syncing state with Okta is one of the trickiest parts
Any sync task should be idempotent
Okta has a lot of limits on its API
All group and approver configurations are in Terraform (Woot!)
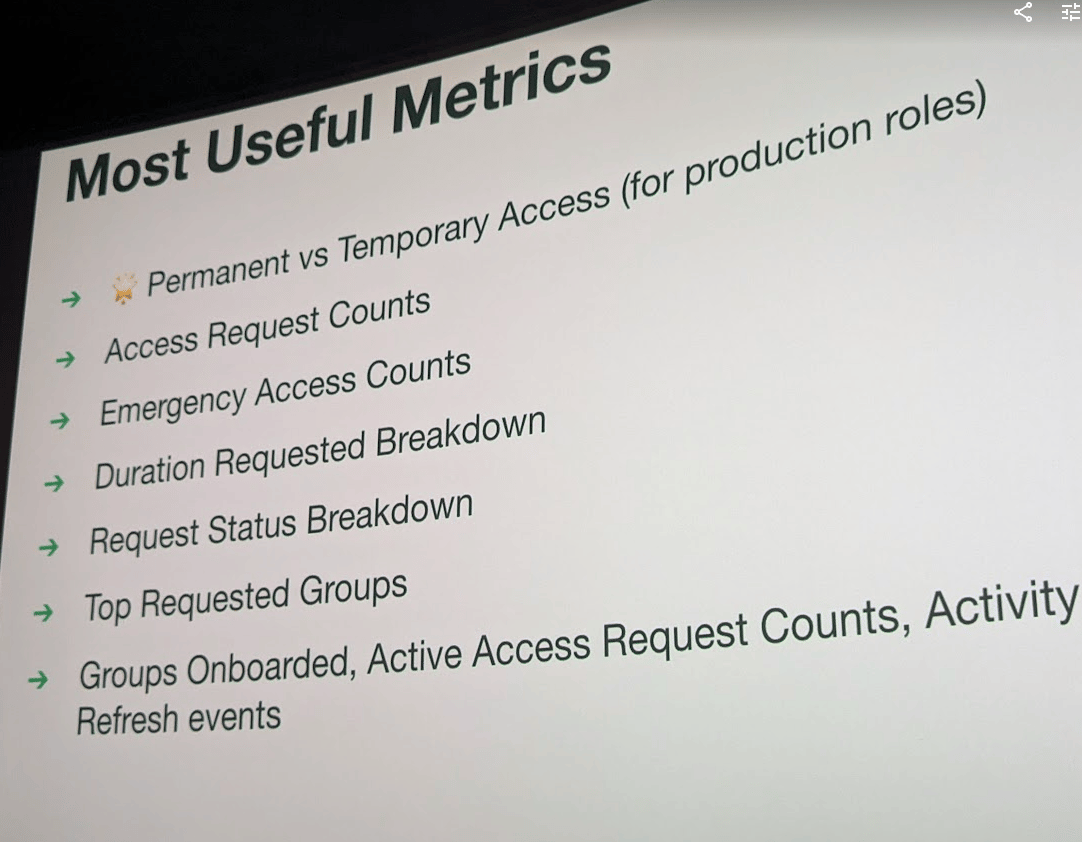
💡Product Metrics are awesome, and can be very valuable for security teams, but are often underutilized!
See Segments “Tracking Meaningful Security Product Metrics”
Took a year to go from first commit to production
Still working on removing ALL permanent access
Dog Food Plan
Use internally in security
Find a champion group
Feedback and iterate
Key: Roadshows for internal engineering teams, leadership, and stakeholders
Pre-Mortem
Changing culture of persistent access
Reduce friction by implementing activity based refresh
Discord’s Open Source Version: Access
Discoverability is still a problem
Committing to temporary access during rollout is super important
Snowflake role level attribution is hard
Can save money on seat licenses!
Lessons Learned:
Start with application group assignments as the foundational entity
Application authentication as a “usage event” will probably get you 80% of the way there
Unfortunately it doesn’t seem like the tool will not be open sourced anytime soon. According to the speaker he built it to be open sourced, and said it would be great if it can be published by the end of the year. It seems like there a tons of specific dependencies preventing the tool from being ready for open source.
Interestingly enough, every company seems to be recreating the wheel. For a fact, this tool has been built numerous times over and over again by groups publicly and privately. It’s a feature Okta could just deploy itself.
In hallwaycon after the talk, met someone who mentioned a newsletter that talks about this specific topic! Thanks Rohit!
Talk: Effective building blocks for securing multi-tenant Kubernetes cluster

Some interesting facts highlighted by the talk (We know this, but good to hear this again).
Kubernetes:
Was not designed for multi-tenancy
Is overly permissive by default
Has built-in escalation paths
It’s fascinating to me how we in tech move to technology so early, and try to make them do things they were not meant to do. The realize that there’s no security built-in. It’s like we all have SNTS (Shiny New Tool Syndrome). 😅
Other Notable Talks
I couldn’t catch them, but here are some talks you should check out
Caroline Wong
Nicole Grinstead
Anna Westelius
Swathi Joshi
Tanvi Vyas
TL;DR: Applying AI to Security by Clint Gibler author of TL;DR Sec
Shoutout To Friends
A shoutout to all the people I got to see at the conference. You all feel like family, especially the organizers of BSidesSF whom with I’ve volunteered with for many years prior.
Myself, Lindsey, and Christina Hasnon (A former bootcamp student!)

Karim Eldefrawy, co-founder of Confidencial.io and Amjad Afanah founder of Stealth Startup

Myself and Mike Privette Founder of ReturnOnSecurity.com (Great Newsletter!)
Myself, Mike Privette, and Sean Sun (Founder of Miscreants) sporting Miscreants.com gear

Marco Palacios and Lauren Arce from Pacific Hackers (phack.org)
